The goal of this entry is to provide information to how Cloudflare proxy works and what are the pros and cons to their global proxy. I’ll explain what is a proxy, what is a CDN and how Cloudflare works by combining the two and doing HTTPS interception.
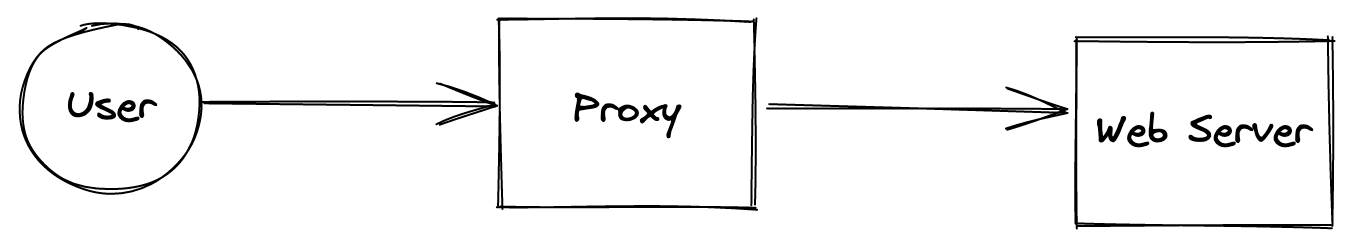
What’s a proxy
A proxy works as a man-in-the-middle for networking traffic. For example when you connect to a company’s website, there is a high probability that you connect to their proxy instead. Then the proxy will forward the connection to one of their server serving their website.
Proxy are used usually to handle SSL connections (encrypt HTTP traffic) and configured to do efficient caching and compression to alleviate the load on the web server behind it.
What’s a CDN
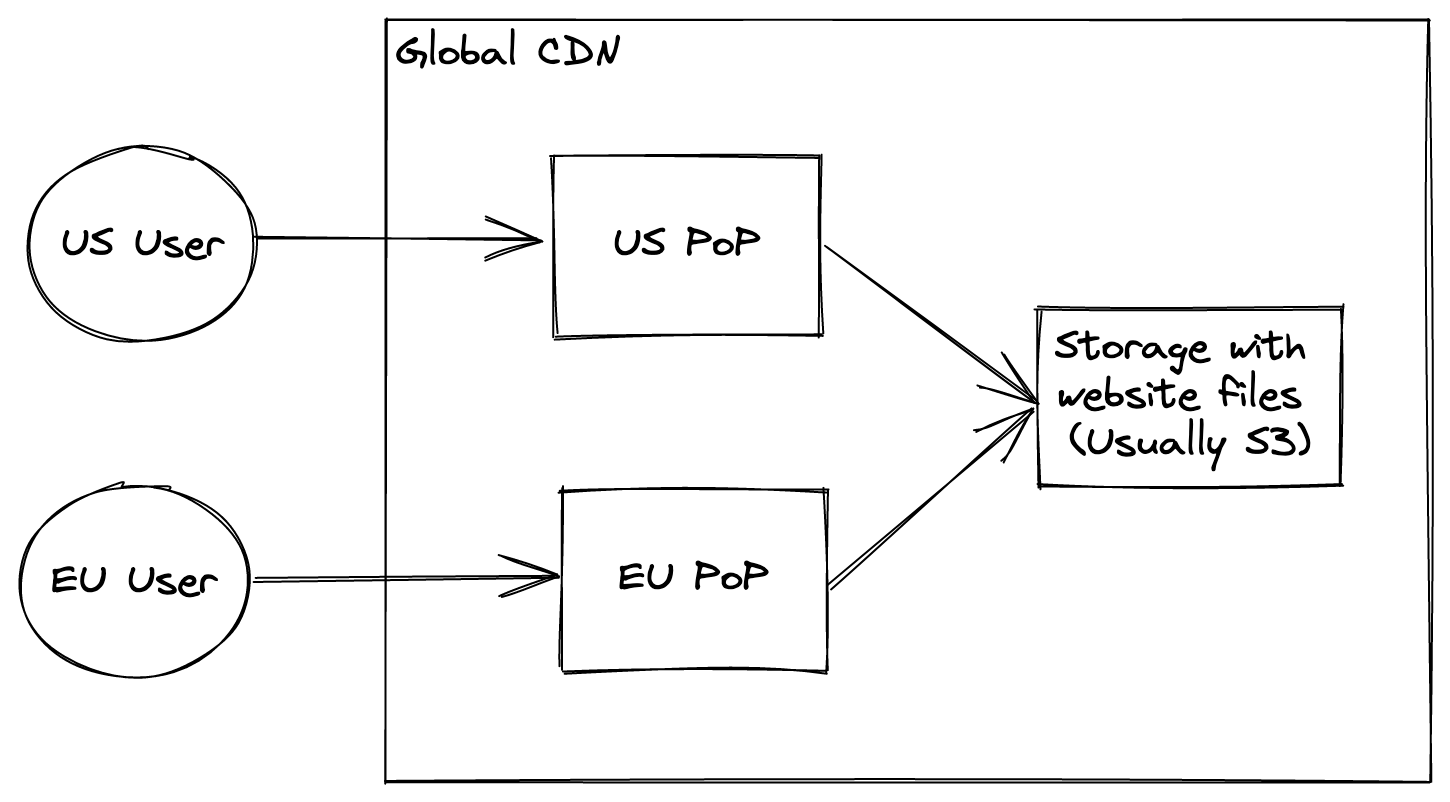
CDNs are products that serve static assets (pre-compiled websites, images, etc…) very efficiently globally. The way they work is that they have multiple points of presence (PoP) around the globe. When a user requests a file, their request is routed to the closest PoP and it can answer blazingly fast.
CDN usually acts as a cache to quickly server files that don’t change often. Examples of this are Akamai, AWS Cloudfront and Google CDN.
Cloudflare DNS Proxy
Cloudflare DNS proxy is effectively a proxy and a CDN in one, that is enabled by the way Cloudflare configures proxied DNS records.
When you add an A or AAAA DNS record in Cloudflare you can select for it to be “proxied” by Cloudflare. What that means is that Cloudflare will not answer DNS requests for this record with your actual IP, but instead with their proxy IP.
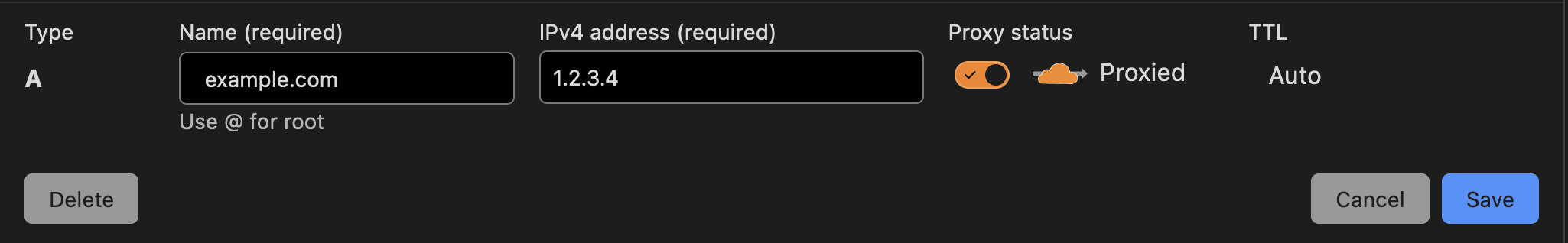
www.example.com A record is supposed to point to 1.2.3.4. Instead of answering with this IP, Cloudflare will answer with IPs that are the closest Cloudflare PoP based on where the request originates from. That means a US user will receive the IP address for Cloudflare’s closest US PoP and an EU user will receive another.
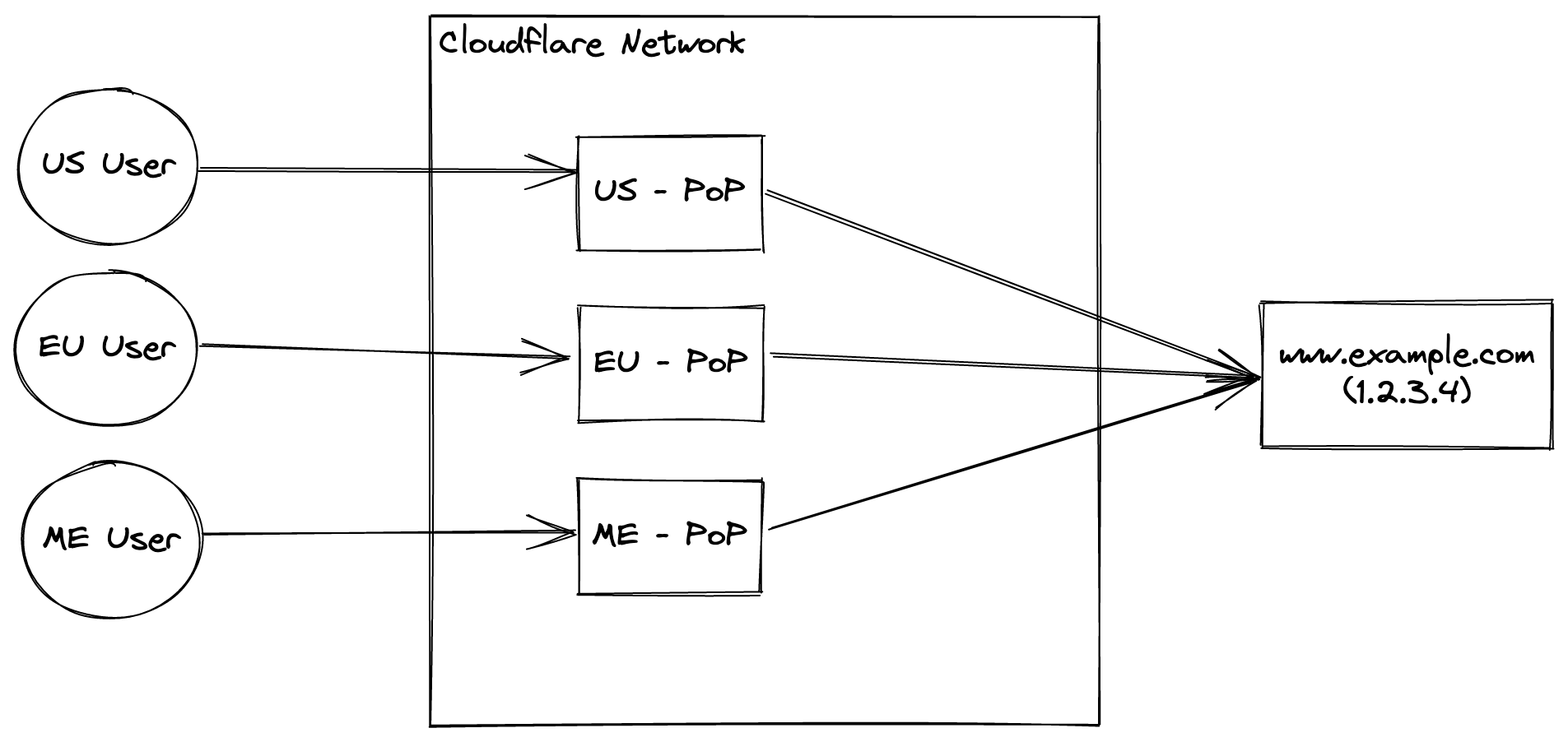
Cloudflare PoPs are not just serving static files. They are intercepting connections between users and your servers, inspecting the connection, and maybe forwarding it to your servers. It might not forward it in those cases:
- It determines if the user is a bot or malicious
- It determines if the user is part of a DDoS attack and engage DDoS protection
- It determines if the request is for assets it has cached and it can return directly
To determine this, Cloudflare man-in-the-middle the HTTPS connection from your users and re-open a new HTTPS connection then to your server. With color, it looks like this.

That is the trade-off offered by Cloudflare. Instant and almost config-less global CDN and proxy with built-in DDoS and malware protection. However, you give up the privacy between your users and your servers.
Most homelab folks build theirs to have more privacy, therefore accepting Cloudflare trade-off goes directly against this. A business would gladly accept this trade-off if it meant better user retention thanks to faster loading time and better security.
The choice is up to you.